September 18th, 2013

A Denial-of-Service attack, or DoS, refers to an attempt by a cyber criminal to interrupt your ability to connect to users. These attacks are launched against websites, networks and apps to disable them, usually by overloading the target with communication requests. In other words, the hackers force the website or network to shut down due to an excessive amount of traffic.
Bob Gorski, of PivotPoint Security, notes that about 65-percent of organizations have experienced three DoS attacks in the past year. The assumption is that hackers target large enterprises like banks and government agencies. However, small business owners need to be prepared for attacks also because their lack of security is attractive to criminals and they also possess valuable data.
The motivation behind a DoS attack can be as simple as an individual being upset at a company. That individual then launches the attack to shut down service and cost that company money. It can also be more complex than that.
DoS attacks have been known to be fronts, or distractions, from more sinister actions. While your security team works to get your website or network back online during an attack, hackers are installing malicious software or harvesting your data.
In another scheme, hackers disabled a site with a DoS attack, then were able to hijack the company;s social media account and redirect users to a phishing site. Users have log-ins and personal information stolen and blame the company.
Firewalls and antivirus software doesn’t protect you from a DoS attack. The best way to be prepared for one is to test. Load testing puts a strain on your website or network to find out if it can handle a DoS attack. This can cause the target to go down, which is why it’s best to run these tests at off-times but when an administrator is available to quickly get your website or network back up.
Geek Rescue helps you prepare for cyber attacks and uses the latest security solutions to safeguard your website and network. Give us a call at 918-369-4335 before an attack causes your business to grind to a halt.
September 17th, 2013

The iPhone 5s will be released soon, which has security experts scrambling to figure out what flaws could be exploited by hackers. Because the new iPhone, and even its new operating systems, iOS7, haven’t been officially released, Matthew J. Schwartz made some educated guesses about possible security concerns at Information Week.
New operating systems usually make sure to shore up any security holes that previous versions may have had. In the iPhone’s case, the previous operating system was considered “a freaking vault” according to one security researcher. The concern then, is that any new operating system will have flaws of its own that are just waiting to be discovered.
A new processor also suggests new flaws to be exploited. But, the new processor promises to make previous exploits obsolete and reportedly makes jailbreaking, or gaining root access to the device through bugs, much more difficult.
Multiple security experts suggest the fingerprint scanner, or Touch ID, will draw most hackers attention initially. There have already been multiple suggestions about how to break through the new iPhone’s security measure.
One tactic, dubbed a “phish finger”, would be to take a finger print from the touch screen and use it to fool the fingerprint scanner. New technology is supposed to make it difficult to fool the scanner without an actual finger, but it can still be done.
Fingerprints of the iPhone’s owner are encrypted and stored on the device, so one theory is that these fingerprints could then be stolen and used to hack into the device. However, the way the fingerprints are stored makes them only recognizable to the iPhone’s processor, which means they can’t be exported to another device.
Touch ID isn’t the only security measure on the iPhone 5s. A password is still in place as well and is required in some situations.
There are certainly some security upgrades on the new iPhone, but there appears to be some potential vulnerabilities as well. In the coming days, more of these vulnerabilities will likely be revealed as more hackers and security experts have hands-on time with the iPhone 5s.
If you need additional security on your mobile device, be it a new or old iPhone, Android or other, bring it to Geek Rescue. We improve security, get rid of malware and fix broken hardware. Come by or call us at 918-369-4335.
.
September 16th, 2013

Apple unveiled the newest entries in the iPhone line recently. The iPhone 5S and a budget model, the 5C. While the 5C features little advantage over last years iPhone 5 other than colored plastic cases, the 5S offers a number of new features.
David Pogue of the New York Times delved into the new iPhone to uncover some of the most interesting new innovations.
If you’re a current iPhone user, how would you rate how fast your phone is able to perform tasks? What if it were twice as fast? The new 64-bit processor in the iPhone 5S promises to double the speed of the previous processor.
There’s also a coprocessor. This assistant handles data for location and motion, which generally takes less processing power. Since the coprocessor operates at only one-sixth of the battery cost of the main processor, this grants you more battery life without sacrificing performance.
Apple has spent relatively little time improving the iPhone’s camera through each iteration. But, for the iPhone 5S they made a real effort. With a better lens and bigger pixels, the camera is better than ever in low-light situations. Color should be improved, as well. The flash is catching everyone’s eye initially, though. That’s because it’s actually two flashes, one white and one amber. One flash fires to gauge the lighting and color of the scene, then the two combine to fit the needs of the situation. There are reportedly 1-thousand lighting combinations the flashes are capable of.
There’s also a burst mode that allows you to shoot ten frames per second. You can use this to rapidly fire pictures, or to shoot video in slow motion.
- The new fingerprint scanner
This one has been the topic of much debate even before the iPhone 5S was officially unveiled. The fingerprint reader is built into the Home button, so securely unlocking your phone just requires a touch of your finger. You can even add fingerprints of others who might be using your phone too. And, Apple lets you use your fingerprint instead of a password when purchasing from Apple’s online store.
The concern has been how Apple stores your fingerprints once they capture them. According to Apple, the fingerprints are encrypted and stored on your phone’s chip. They are not sent or stored online.
The iPhone 5S and 5C will both be available to the public on September 20th. Whether you plan to buy the newest iPhone or not, Geek Rescue has you covered. We’ll fix the newest gadgets if you have an unfortunate accident. Or, we’ll fix your older device to make it seem like new. Call us at 918-369-4335 or come by Geek Rescue with any of your broken gadgets.
September 16th, 2013

There are many elements that make up a proper security infrastructure. But, whether you are looking to improve security at home, or at your business, the first place to look is at your first line of defense, the firewall.
Robert Lemos reports for Dark Reading that fewer users are focusing on their firewall to improve security, which is unwise considering “networks have become more porous” with advancements in technology. Once you decide to improve your firewall, here are some tips.
- Know your firewall’s capabilities
Chances are, the firewall you have in place is capable of much more than you think. Intrusion prevention, web filtering, virtual private networking and secure device management are all common features of today’s firewalls. However, you the user must use the firewall’s settings to get all the advantages of the improves technology. So, before you decide you need to add security, make sure you understand the capabilities of the security you already have in place.
If your firewall is capable of web filtering, make sure you have enabled and fine-tuned that function. If it doesn’t, contact Geek Rescue and ask about our Safety Net. A web filtering service allows you to control the bandwidth used on your network and block sites that are inappropriate or potentially malicious. At home, this means protecting younger users from content that isn’t age appropriate. For businesses, this means blocking sites that are distracting to employees, like shopping and social media. For any network, it’s important to block sites that will infect your network with malware.
A firewall will keep a record of its activity. If you experience an attack, the evidence will appear in the log. It’s important to analyze the firewall’s log to catch any infection or attack before it does serious damage. The problem you’ll find when looking through the logs is the number of false positives you’ll run across. So, you’ll want to do some research so you’ll be able to tell what is important and what isn’t.
Even more than antivirus software, firewalls are vital to security. They’re capable of blocking malicious software and sites before they have a chance to infect your computer. They’re capable of much more too.
To enhance your network’s security for home or business, contact Geek Rescue at 918-369-4335.
September 13th, 2013
Viruses and malware are a constant threat for PC users, but Mac users have been able to avoid most of the security threats over the years. One prominent threat recently suggests that security for Mac users may be more important than ever before, however.
Samantha Murphy Kelly of Mashable reports that a malware threat targeting Macs has been discovered on compromised websites.
The threat likely won’t affect most of Mac users, particularly in the US, because it was discovered on anti-Chinese websites hosted in Tibet. It also relies on Macs using Java applets on the web, which is a minority of users.
This malware threat is a concern, however, for a few reasons. Namely, the malware used gives hackers the ability to access remote files and monitor a user’s activity on their device. The fact that it targets Mac users is also concerning because of the lack of security on many machines. Finally, this malware wasn’t disseminated through spam email or downloads. Simply stumbling onto the wrong website could infect your computer.
So, while this particular attack likely won’t infect your computer, it does suggest that more security is necessary even for Mac users. If cyber criminals can deploy an attack of this nature in Tibet, they could certainly do the same on a site closer to home.
To enhance the security on your machine, be it Mac or PC, contact Geek Rescue at 918-369-4335. We not only offer a variety of security options for a variety of devices, but we also fix and clean devices with malware or virus infections.
September 13th, 2013

Recent reports show that tablets are overtaking laptops in number of units shipped. With more and more tablet users out there, they become a much more attractive target for cyber criminals.
As Daniel Mellinger writes for IT Toolbox, most tablets must be linked to an email account and some even hook to mobile phone accounts. They’re used to access bank accounts, credit cards and do online shopping. This means they are home to an abundance of valuable data.
Much like the lack of security on smartphones, many tablet users decline to even have a password required to unlock the device. Not only should you set up a more secure way to unlock your tablet, but you should also consider downloading one of the numerous biometrics apps that will add a finger print scan or additional level of security.
There’s also the question of what happens if your tablet is lost or stolen. Whoever finds it will have access to all the sensitive data you’ve stored on it. Consider signing up for a remote wipe service. There are a number of easy to set-up third party apps. If you have an Apple or Android device, there are native options to use, as well. The idea is to be able to erase anything stored on the device so that whoever now has it can’t access any of your data.
Another security concern is malware. Tablet specific attacks will be more common with the tablet audience growing rapidly. This means you need security software in place. You run the risk of malware when you click on a link, download an email attachment or visit a malicious website. Most users aren’t aware that they’ve downloaded malware until it begins to affect their device’s performance. Malware is capable of harvesting data, monitoring activity and even hijacking some functions of your device.
Malware infections lead to hacked email and social media accounts, stolen identities and compromised bank and credit card accounts. That’s why it’s important to practice safe surfing and have robust security apps in place.
For help upgrading the security on your tablet, smartphone or any device, contact the experts at Geek Rescue by calling 918-369-4335.
September 12th, 2013

A new form of malware attack on Android phones has security experts on the look-out. This form of scareware infects your computer through a phishing email and malicious link.
Chris Brook, of ThreatPost, reports that the emails will appear to be from the United States Postal Service.
The message informs you that the USPS was unable to deliver your package because the postal code contains an error. You’re then prompted to print a label. When you follow the “Print The Label” link included in the email, a malicious Android Package File, or .apk, is downloaded to your device.
This particular scam seems poorly constructed. After all, most of us know when we’ve sent a package recently and understand that printing a label for a package that isn’t in our possession wouldn’t do much good. However, there are plenty of users who will click the link to try to gain more information, even if they haven’t sent a package in months. Hackers play on our curiosity and even thin attacks like this one will claim victims.
This form of malware has been used before. Security experts note that a previous scam using it in a scam that asks users to pay a subscription fee to keep their devices clear of malware. What’s noteworthy is the way the malware is being distributed. Cyber criminals are adjusting to the number of users who access their email on their Android devices and are attempting to exploit that fact.
This malware is reportedly even capable of intercepting both incoming and outgoing calls. It also is capable of changing file names to look more innocent. Instead of a suspicious .apk file, it will appear as a .zip file with a tantalizing name like vacationphotos.zip.
Android users should go into the settings on their device and disable the option to “allow installation of apps from unknown sources”. Users will also be able to enable a “Verify Apps” option, which will warn them before any potentially malicious app is downloaded.
These two options help keep your device safe, but you’ll also want dedicated security apps as well. To upgrade the security on any of your devices, or to rid them of existing infections, come by or contact Geek Rescue at 918-369-4335.
September 12th, 2013

For users of the web browser Google Chrome, a new malware threat has emerged. This threat looks a lot like Candy Crush and Super Mario.
Eric Johnson, of All Things Digital, describes the “wild west” atmosphere of the Chrome Web App store. Unlike Google Play, the app store for Android mobile devices, Chrome’s Web App store is much less regulated.
This lack of regulation has lead to a number of knock-off apps. Mostly, these apps are recreations of famous games like Super Mario, Candy Crush Saga, Fruit Ninja, Doodle Jump and Sonic the Hedgehog. These games aren’t licensed by their original creators and many are suspected to contain malware.
It’s not hard to understand why malware is included in these recognizable games. Users see a game they played in their youth, or a game they’ve heard is popular now, and want to try it out. It’s a naturally attractive app for what seems like no obligation. However, the apps are usually poor quality and infect your computer with malware.
The key to spotting these knock-off, malicious apps is simple. First, understand that Nintendo, Sega and other giant game companies aren’t making officially licensed apps for Chrome. If you have any further questions, look at the website associated with the app. In the case of a Candy Crush Saga knock-off, the website was listed as candycrushsaga.blogspot.com, which is not associated with King, the game’s developer.
If you have added one of these apps or another app you think contained malware, run your fully updated virus scan after you remove the app from Chrome.
For additional security on any of your devices, contact Geek Rescue at 918-369-4335. We offer security solutions to keep you safe from malware, spam email, viruses and more.
September 11th, 2013

Many small business owners believe that they won’t be the target of a cyber attack simply because there are larger companies that present more value to hackers. However, this belief leads to more relaxed security protocols, which makes small businesses an attractive target because of their ease of access.
Susan Solovic posted on the AT&T Small Business blog how to immediately improve your company’s security without having extensive expertise.
As with any account, you need to protect your business by having each employee log-in with a secure password. This password should be long, have upper and lower case letters and symbols and numbers and be changed often.
It’s a basic step that pays big dividends. Don’t make it easy for a criminal to steal your information or infiltrate your network. When you’re not sitting at your computer, sign out. This erases the possibility that someone in the area could walk by and immediately access valuable data. This is especially important for mobile devices.
There’s a reason your antivirus software requires regular updates. Hackers are constantly changing tactics and using new techniques. Each update is an attempt to stay ahead of the curve. So, when any of your regularly used applications prompts you to update, do it.
Nothing keeps you 100-percent secure. Even if you are able to avoid a cyber attack, natural disasters could still wipe out data. Regularly backing up vital data is important in order to avoid a catastrophe. Should any of your files be lost or corrupted, you’ll have back-ups to replace them quickly without suffering any down time.
Each employee and each position at your company is different. Some will require different access to different applications. Think of it like a government security clearance. There are different levels depending on your pay grade. For your business, give employees the access necessary for them to do their job, but no more. This way, if their account is compromised, you won’t be allowing access to your entire network.
Keeping your business secure is an important and time consuming job. For help, contact Geek Rescue at 918-369-4335. We offer data storage and back-up, security solutions and more.
September 11th, 2013
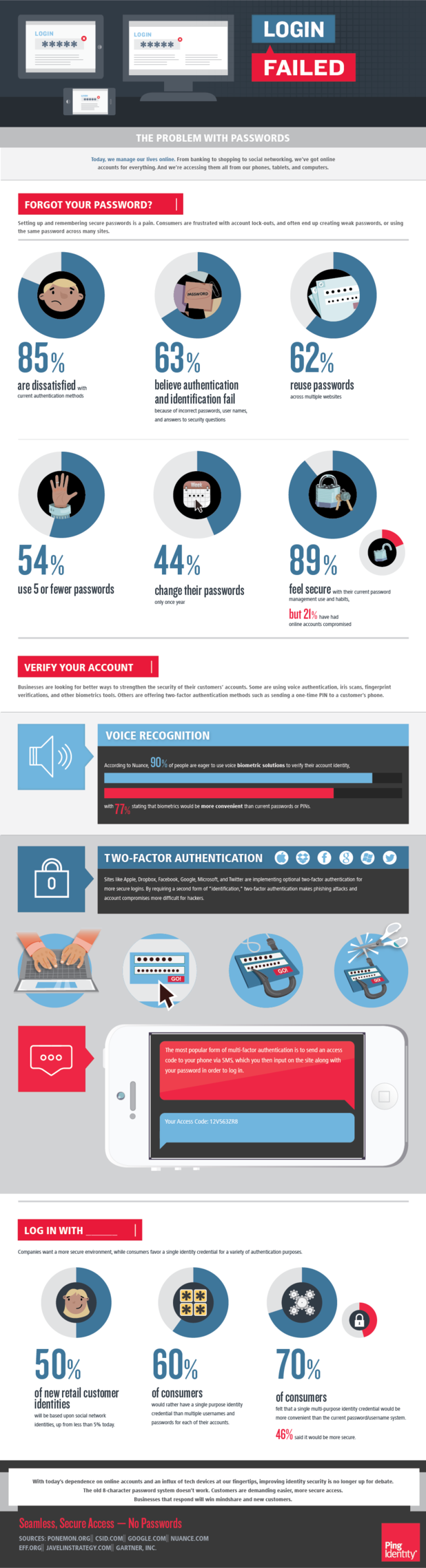
Would you call your passwords to the various accounts you have online secure? It depends on how many characters your password is, if you use upper and lower case letters, symbols and numbers, if you use full words, recognizable names or places from your life and whether you reuse passwords on multiple sites.
Ping Identity’s Christine Bevilacqua published a blog along with the included infographic that speaks to the problem with password security.
Many of us have experienced a compromised online account and a broken password is often to blame. There is software readily available that is capable of breaking even incredibly long passwords. Sometimes, the strength of your password isn’t even the issue.
In the case of the latest attack on the New York Times, a spear phishing scam resulted in an employee giving out their password. Cyber criminals have become increasing intelligent about creating ways to hack into your accounts.
If you aren’t scammed into giving out your password outright, you may be guilty of clicking a link or downloading an attachment you shouldn’t have. This could infect your computer with malware capable of monitoring your activity, stealing passwords and infiltrating your accounts.
Some online accounts are moving to require a log-in with social media accounts, but what protects your social media accounts? A password does.
One of the latest innovations on the new iPhone is the use of biometrics. In order to unlock the phone, users will use their fingerprint. This seems like a foolproof plan. Afterall, no one will be able to hack into your phone unless they have your fingerprint. However, the problem becomes the unreliability of biometrics. For example, what happens if an error occurs and your phone won’t recognize your fingerprint? For most similar systems, the fall back is simple password protection, which brings us back to square one in terms of security.
The key to avoiding a hacker cracking your password is to practice safe surfing techniques and to have the latest security software in place.
To make any of your devices more secure, contact Geek Rescue at 918-369-4335.




















