November 27th, 2013

A new piece of malware, a trojan called ‘Neverquest’, has security experts scrambling and forecasting a number of future attacks. As Lucian Constantin of Computer World reports, Neverquest has the ability to spread quickly and steal your financial information.
It’s believed that the Neverquest trojan originated in July, but the first attacks didn’t occur until months later. Now, experts have spotted thousands of uses of Neverquest and they expect to see that number spiral out of control soon.
In many ways, Neverquest is similar to other malware that targets financial websites. It’s able to insert its own forms into websites opened in Internet Explorer and Mozilla Firefox. It steals log-in information entered into these malicious forms and can also control your computer remotely.
Those are scary features, but that’s not all Neverquest can do. The trojan comes with 28 websites where criminals will be able to steal log-ins that control finances. These are the most popular banking sites and online payment services. To expand the number of sites it’s used with, and to ensure that every infected user is at risk, the trojan also monitors a victim’s activity and searches sites visited for keywords like ‘account summary’ or ‘balance’. When it discovers those sites, it alerts it’s host so they can begin attacking those sites as well.
In order to gain access to your computer, hackers first infect websites. When you visit one of these infected websites, vulnerabilities in browser plug-ins are used to install malware directly onto your hard drive. Spam email and links sent over social media are also used to infect users.
To keep your computer, and bank account information safe, don’t follow suspicious looking links and don’t visit untrusted websites. Keep your antivirus program running and up to date, as well.
If you have malware, trojans or viruses on your computer, bring it to Geek Rescue or call us at 918-369-4335. We clean infected machines and help you protect against future attacks.
November 21st, 2013

Spam emails began as a nuisance, but one that ultimately wouldn’t harm your computer. Since those early days, spam has evolved to be much more malicious. Now, spam often is the first step to infecting your machine with malware, trojans, keyloggers and viruses. Spam can be used to steal your identity and hold your computer for ransom. Jeff Orloff of The Email Admin posted some threats to be on the look-out for and some tips for how to stay safe.
Cryptolocker is the latest threat making headlines. The trojan is a form of ransomware that first surfaced in August. Most commonly, it stems from an email attachment that infects the victims computer when it’s downloaded. The cryptolocker is then able to encrypt certain types of files on your system and holds them for ransom. To decrypt the data, a payment is required. Often, there is a deadline that goes along with this demand for money. While some users report they’ve paid the ransom and their files were encrypted, others have paid and seen no results. Unfortunately, even professionals struggle to decrypt files that have fallen victim to a cryptolocker.
In less than a week, more than 12-thousand users reported being infected by a cryptolocker in the US. This isn’t the only threat to your security that strikes through email. Cryptolocker is just the latest.
Email security is essential for both your business or your home network. There are a number of options for enhanced email security, but regardless of what you choose, make sure it includes some vital features. Your security software should scan incoming email for known threats and separate those that are potentially harmful. Email protection has to be more intelligent than ever to properly protect you. Spammers are constantly updating their tactics to get around spam filters.
Geek Rescue offers a number of options to keep you safe from the latest cyber threats. Call us at 918-369-4335 to find out how we can protect you.
November 15th, 2013

It seems like every week a large-scale password theft makes headlines. The latest was Adobe, who experienced the loss of about 150-million user log-ins. Michael Santarcangelo, of CSO, writes that anytime a large batch of log-in information is stolen it jeopardizes the security of other businesses. There are three steps that should be taken in this event to keep your business secure.
- Check The Email Addresses
When an attack of this nature occurs, the compromised log-in information is made public. If you know where to look, you can look through the list of stolen log-ins for email addresses in your domain. This is important because if an employee had information stolen for one account, it significantly increases the likelihood that their other accounts could be compromised. This could lead an attack to your network. If you see one of your addresses in the list of compromised accounts, be sure to notify the owner of the address, then change their log-in information for your network.
Every password that was stolen is now in a hacker’s database. That means that any individual who uses the same or similar password as a user who had their account compromised is now in danger. Hackers will use these learned passwords to launch more informed, intelligent attacks on accounts. Check your company’s log-ins for similar passwords and get them changed immediately.
Be sure to explain to the affected employees why their account log-ins need to be changed and how a hacker could attack them. Giving them access to better information and training could prevent an attack in the future.
Few business owners understand that the loss of a large group of log-ins and passwords, such as the Adobe situation, could affect them also. Taking these precautions is labor-intensive, but necessary for security.
For help protecting your company from a devastating cyber attack, contact Geek Rescue at 918-369-4335.
November 14th, 2013

Spam email is a common problem for anyone with an an email address. Most spam messages are easy to identify, but a practice called brandjacking muddies the distinction between legitimate email and spam. Sue Walsh, of the All Spammed Up blog, reports that a recent brandjacking spam campaign involves Dropbox and attempts to steal banking and credit card information.
This scam starts when an email that appears to be from Dropbox arrives in your inbox. There are multiple variations of the same spam email, but all contain the same basic message. Some, however, are more convincing because they eliminate the typical broken English and poor spelling that marks most spam.
The message informs users that their password is too old and needs to be replaced. Users are then directed to follow the provided link and update their password. This is actually a believable ploy because Dropbox does periodically ask users to change passwords when their account hasn’t been active for an extended period of time.
The link provided doesn’t take users to a Dropbox log-in page, however. Instead, they arrive on a site made to look like it’s owned by Microsoft and told that their browser is out of date. An update is offered up for download, which is actually a Trojan that steals banking and credit card information.
The same group suspected of this scam has brandjacked UPS, Verizon and the Better Business Bureau in the past.
No matter how believable a message is, there are still ways to see through these scams. Before following the instructions of any email, check the sender’s address. In this case, the send won’t have an ‘@dropbox.com’ address, so you can assume the message isn’t legitimate. Also, if you follow a link provided that doesn’t take you where it’s supposed to, it’s another sign that you’re being scammed.
If you have any suspicion that an email you receive from a company isn’t legitimate, contact the company directly by phone.
If your computer has been infected by malware, viruses or Trojans, or you’d like to improve your device’s security before an attack happens, contact Geek Rescue by calling 918-369-4335.
November 11th, 2013

A zero-day exploit that affects Internet Explorer, Windows XP and Windows 7 users won’t be getting a patch from Microsoft any time soon. Microsoft’s Patch Tuesday for November is only a day away and, as Paul Ducklin of Naked Security reports, news is already spreading that a patch for this exploit won’t be included.
The “remote code execution vulnerability” is dubbed a zero-day because hackers were the first to discover it. Rather than security experts, or Microsoft themselves, discovering the vulnerability and patching it, cyber criminals have been able to launch attacks in the wild before any precautions could be taken.
The attacks seen so far that exploit the vulnerability use .TIFF image files that contain malware. When a user opens the seemingly innocent image file, malware infects the machine, but no warning or notice is given. This silent infection allows hackers to remain undetected while they claim access to files and control a computer remotely.
So far, most of the attacks stem from email attachments. The .TIFF is hidden in a Word document and automatically loaded when the document is opened. There are a number of other ways the exploit could be attacked, however. Inserting the infected image file directly into the body of an email could infect your system through only a preview of the message. Hackers could also set-up websites specifically to infect visitors, or insert malware into existing sites using .TIFF images.
While there’s no patch coming from Microsoft this week, there are ways to protect yourself. A Fix it tool released by Microsoft will tell your computer to stop processing .TIFF files. This is a broad stroke, but one that will ensure the vulnerability will be closed until a more permanent patch is made available.
In the meantime, some simple advice will also help improve your security. You should always be wary of unsolicited emails and their attachments. Often, all it takes is opening the email to try to verify its authenticity is all it takes to become a victim. Also, make sure you have an antivirus program in place and it’s updated. Because of the way this exploit gives a hacker access to all of the files you’re current user account is able to access, it’s useful to use a non-administrator account. That way, if you are attacked, only part of your system is at risk, and solving the problem from an administrator account is much easier.
If any of your devices are infected with malware, bring them to Geek Rescue or call us at 918-369-4335. We’ll find the problem, fix it and help you protect yourself from future attacks.
November 5th, 2013

Spam is everywhere online. An estimated 14.5-billion messages categorized as spam are sent every day. It’s not just your email inbox that’s being bombarded either. Comment sections, social media and even text messages are also being hit. A post at the All Spammed Up blog writes that we only have ourselves to blame for this barrage of spam.
Electronic spam is an umbrella term that refers to any unsolicited, mass message usually used for advertising purposes. It’s the online equivalent of junk mail addressed to ‘Resident’. Recently, it’s also been adapted to spread malware. The reason it exists and is expanding is that it works. Those who are sending out spam messages are finding it to be a worthwhile endeavor and a profitable one. The key to stopping it is for users to get smarter and stop falling for it.
Messages pour into your email every day and most of them are caught by a filter and placed in the spam folder. Still, some spam gets through to your inbox. Your phone even receives spam text messages, although not nearly as many as your email sees. The reaction of most people is to delete the obvious spam, but it keeps coming because there are those that don’t. You can’t control what other people do, but you can control how often you give out your contact information. If you want to stop spam from coming to your phone, stop giving out your phone number so indiscriminately. If you want to stop, or at least decrease spam email, be more careful who you give your address to. For any site you feel is questionable, use an alternate email instead of your primary address.
Spam on social media is a slightly different animal. The spam often comes from seemingly legitimate accounts of friends that have been hijacked. There are also dedicated phony accounts whose sole purpose is to send out spam and malicious links. Sites like Twitter and Facebook do take down phony accounts when they find them. If users stop clicking on these links, those spam accounts would disappear. To keep accounts from being hijacked, users need to surf safer. Accounts can be hacked in a number of ways, but usually it stems from clicking a bad link or downloading malware.
The comment sections of blogs, news sites and social media sites like YouTube and Instagram are often home to spam messages. They’re easy to distinguish from legitimate comments because they usually don’t have anything to do with the page their commenting on and almost always include a link. But, they use social engineering to entice users into following the link. Common tactics are promising high paying, work from home jobs, or cheap electronics. Most users know better, but follow the link to find out for sure whether it’s a legitimate offer. Blog and website owners usually delete these spam comments when they see them, but the spammers often combat this by including a compliment of the site and playing of the owner’s ego.
If no one fell for these spam messages, spammers would stop using these tactics, but probably evolve into something else. The keys for avoiding spam is to surf safely, have a trusted spam filter in place on email, resist offers that are too good to be true and generally be wary of links.
Geek Rescue offers protection from spam and malicious websites with out Safety Net program. We also clean and fix computers that are infected with malware. Call us at 918-369-4335 or stop by one of our convenient locations today.
November 4th, 2013
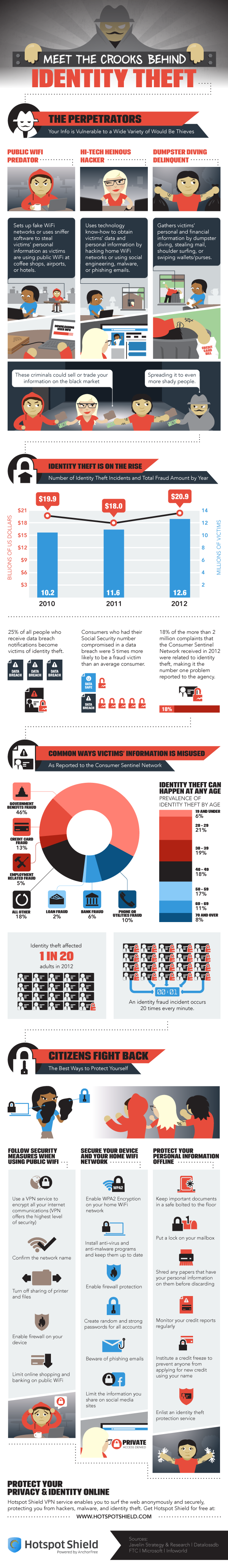
Protecting your computer from viruses and malware is only part of the concern of cyber security. Identity theft, which often begins with data being stolen over unsecure networks, through malware, or phishing scams, is also a costly threat.
Peter Nguyen, of the HotSpot Shield blog, writes that the number of identity thefts in the US is constantly growing. Last year, there were 12.6-million victims, which is enough for an identity theft to happen every 3-seconds. The financial loss of the victims totaled almost $21-billion.
The included infographic covers the how and why of identity theft. It also gives a few tips for how to stay safe. In addition to some offline measures, like shredding documents containing personal information, monitoring your credit reports, and locking your mailbox, here are the most important online safety tips.
- Beware public WiFi. When using an unsecured network at a coffee shop or other public place, limit your activity. Any transactions that require you to input financial information should wait. A firewall should be enabled on your device and you should turn off sharing of printers and files.
- Use proper security on your home wireless router. The router is your first line of defense, so make sure WPA2 encryption is enabled and a strong password is required to log on.
- Keep antivirus programs running in the background and keep them updated. Updating security software enables them to detect and protect against the latest threats.
- Keep social media profiles private. Every social network gives you options for what you share with whom. Make sure strangers don’t have access to information like your birthday, family information, phone number and employment history. This can all be used for identity fraud.
- Use long, strong passwords. Many security experts suggest passwords longer than 6-characters and using both upper and lowercase letters, numbers and symbols.
To improve the security of your devices at home, or at your business, call Geek Rescue at 918-369-4335. We not only fix devices, we also help keep them safe.
November 4th, 2013

What do you know about CrytpoLockers? As a post on the Integral IT blog reports, this relatively new form of computer virus is capable of gaining access to and encrypting files on your machine, which then makes it impossible for you to use them. In order to stay safe and minimize the damage, there are some precautionary steps that need to be taken.
CryptoLockers primarily gain access to your computer or network through email. They appear as a seemingly legitimate attachment. Once downloaded, they begin to wreak havoc.
Any file you have access to, a CryptoLocker will encrypt and damage. You’ll no longer be able to access these files. When you try to open them, you’ll be met with a warning that the file is corrupted and can’t be opened.
This warning is the first sign that you’ve downloaded a virus. Otherwise, the CryptoLocker operates in the background and is undetectable for most users.
To remove the virus, you’ll have to identify the file containing the CryptoLocker and delete it. Then, you’ll be able to restore the corrupted files from back-up, which you’ve hopefully kept current.
To avoid a catastrophic loss of data due to a CryptoLocker infection, keep a trusted, frequently updated antivirus program running on your machine. Allowing it to update constantly makes it more capable of detecting new threats like CryptoLockers before they do any real damage.
Be aware of threats like this when checking your email. Using attachments is a popular method of hackers for infecting a large number of users. Knowing this makes you more suspicious of emails containing attachments, especially when they’re unsolicited.
This is also a warning to keep your back-ups current and frequent. You’ll never be able to be immune to threats like this, so regularly backing-up vital files ensures that, even when disaster strikes, you’ll be able to recover quickly.
Geek Rescue offers security solutions for all of these issues and concerns. We remove existing viruses and malware, improve your security infrastructure to better protect against threats and offer data storage and back-up. Call us at 918-369-4335 to stay safe from threats like CryptoLockers.
October 29th, 2013

Apple recently released their new operating system for Mac users, OS X 10.9 Mavericks, and made it free to download. Similar to the early days of iOS7 for iPhones, however, Mavericks has had a rocky start filled with bugs. Apple will have to release an update for some of the more serious problems, but, as Roberto Baldwin reports for Wired, there are some fixes any user is capable themselves. Here’s a look at some of the simplest.
Even before getting to install the new operating system, many users are encountering problems. Slow or stalled downloads have plagued the release, but there are some easy fixes. If your download is taking forever, go to Launchpad, the Mavericks download may be paused. In that case, just click the icon and it will resume. If it’s still too slow, hold down Option until the app icons start to bounce, then click the ‘X’ by the Mavericks download to cancel it. Try to download again from the App store and it should download much faster.
Scrolling up and down seems to be disabled in certain apps, including the Google Chrome web browser. To fix the problem, you could completely delete the app, then re-install. That has worked for many users. However, if you’d rather go through that process, you can instead navigate to ‘System Preferences’ in the Finder. Then go to ‘General’, ‘Show Scroll Bars’ and select ‘Always’. This brings back your scrolling options for all apps.
For enhanced security, an email client that refuses to remember your password is a good thing. Most users find it incredibly frustrating to have to put in their password every time they check their mail on their own machine, however. If Mail is forgetting your password, fix it by going to the Menu Bar, then select ‘Mail’ and ‘Preferences’. Click the Accounts tab and change ‘Authentication’ to ‘Apple Token’.
Other issues encountered so far in Mavericks include Gmail not working correctly, problems with QuickLook and slow or stalled shutdowns. Apple is working to patch some of these and others require some advanced knowledge to overcome.
For help fixing these bugs in the Tulsa area, come by or call Geek Rescue at 918-369-4335. We also fix broken machines and those infected with malware or viruses.
October 18th, 2013

Everyone has heard warnings about the dangers of spam. The term ‘spam’ is pretty general, however. The best way to stay protected from it is to understand what it looks like and avoid it.
A post on the All Spammed Up blog breaks down the different types of spam and the tell-tale signs of each.
Not all types of spam are malicious in nature. Some emails that end up in your spam filter are examples of overzealous marketing. They’re usually from a trusted company that you’ve given your email address to at one time or another. There’s a reason they’ve been marked as spam, however. That’s either because their marketing messages come far too often, or they offer little to no value. Whether these are arriving in your inbox or spam folder, you’ll probably want to unsubscribe.
This type of spam isn’t from reputable companies but is hocking some sort of product. Usually it’s supplements, education or financial services. They’re sent out in bulk and not personalized to a single user. Usually, you’ll even be able to tell that there’s a long list of email addresses listed as recipients. These are sent out by individuals who get money each time someone clicks the links in the emails or signs up for the products offered. The products are worthless, if they exist at all. If one of these arrives in your inbox, mark it as spam and move on.
This type of spam email attempts to steal information from users. Many have malware attached to them, or direct you to a malicious website that will download malware to your machine. They use social engineering to convince you to give up information like account log-ins and passwords. There are more specific attempts called spear phishing, that target small groups of people in order to obtain specific information. These types of attacks will appear to know a great deal about you. In order to avoid these scams, it’s a good idea not to follow links provided in emails and never download attachments unless you are expecting them from a trusted source.
This is similar to phishing and can even be combined with a phishing scam. An email arrives claiming to be from a legitimate source that you have an account with, like Facebook, Verizon or even a credit card company. It usually tells you there’s a problem with your account and you need to log-in by following the link provided. This link will take you to a different site where your log-in information will be recorded and used to hack your account. Again, don’t follow links provided in emails. If you want to check out the legitimacy of an email, go to the source’s site directly, or call them. Also, check the sender’s email address. A representative of Facebook, for example, will have an email ending in @Facebook.com. Many of these scammers have email addresses like FacebookHelp@ccvs.com.
Knowing what to look for is key to avoiding email scams. Improving the security on your email and your computer are also important.
For help bolstering your cyber security, either at home or at the office, contact Geek Rescue at 918-369-4335.




















