November 15th, 2013
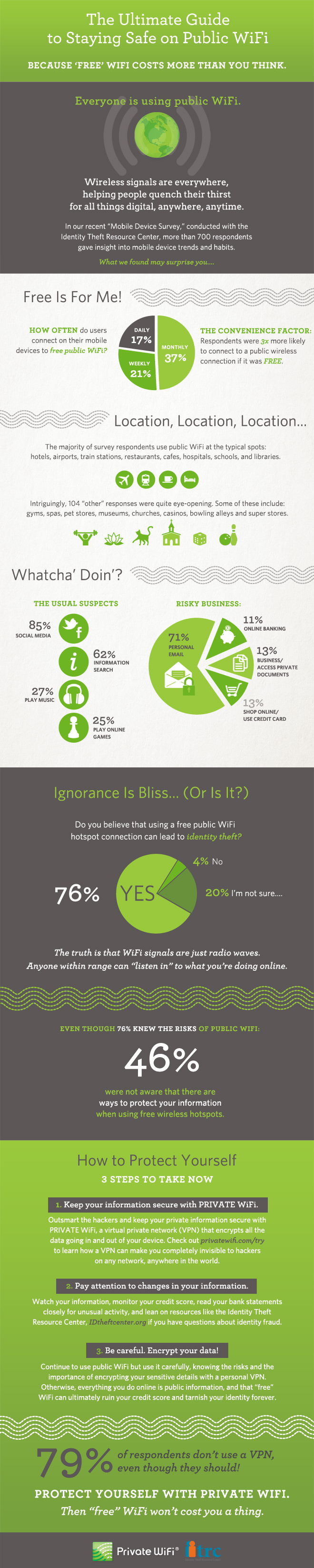
Free, public WiFi is offered nearly everywhere. Whether you’re at a library, coffee shop, restaurant, hotel, airport or hospital, you’ll be able to stay connected. That free WiFi comes with some inherent risks, however. PrivateWiFi and the Identity Theft Resource Center teamed up to produce this infographic, which details the general feelings about free WiFi and how you can stay secure while using it.
More than three-quarters of users understand that public WiFi isn’t secure. That’s the first step in a safer experience because those users will know not to log-in to their personal email or banking site while using an unsecured network. These safe surfing tactics aren’t the only way to improve security, however.
If a public network is unsafe, then why not use a private network? Even when connected to public WiFi, you can use a VPN to immediately improve security. There are a number of VPNs available. While many require a paid subscription, some are free up to a certain point. The VPN encrypts data being sent by your device and the data being returned to it.
A good idea is to keep close tabs on your online accounts, your financial information and your credit score regardless of the kind of network you’ve been using. But, it’s especially important to monitor your information if you know you’ve been on a public network. You probably won’t know immediately if someone hacks into your bank account or steals your identity. Regularly checking this information will save you from devastating damage because you’ll be able to recognize the first signs of trouble.
Understanding what’s at stake and when your information is most vulnerable is an effective way to stay more secure. When using free WiFi, try to avoid any site that require you to log-in. If you absolutely must log-in over an unsecured network, look into putting a VPN in place before doing so.
With more and more free wireless networks available, it’s more important to learn how to safely use them.
For more help improving the security of any of your devices at home or at the office, call Geek Rescue at 918-369-4335.
November 14th, 2013

Spam email is a common problem for anyone with an an email address. Most spam messages are easy to identify, but a practice called brandjacking muddies the distinction between legitimate email and spam. Sue Walsh, of the All Spammed Up blog, reports that a recent brandjacking spam campaign involves Dropbox and attempts to steal banking and credit card information.
This scam starts when an email that appears to be from Dropbox arrives in your inbox. There are multiple variations of the same spam email, but all contain the same basic message. Some, however, are more convincing because they eliminate the typical broken English and poor spelling that marks most spam.
The message informs users that their password is too old and needs to be replaced. Users are then directed to follow the provided link and update their password. This is actually a believable ploy because Dropbox does periodically ask users to change passwords when their account hasn’t been active for an extended period of time.
The link provided doesn’t take users to a Dropbox log-in page, however. Instead, they arrive on a site made to look like it’s owned by Microsoft and told that their browser is out of date. An update is offered up for download, which is actually a Trojan that steals banking and credit card information.
The same group suspected of this scam has brandjacked UPS, Verizon and the Better Business Bureau in the past.
No matter how believable a message is, there are still ways to see through these scams. Before following the instructions of any email, check the sender’s address. In this case, the send won’t have an ‘@dropbox.com’ address, so you can assume the message isn’t legitimate. Also, if you follow a link provided that doesn’t take you where it’s supposed to, it’s another sign that you’re being scammed.
If you have any suspicion that an email you receive from a company isn’t legitimate, contact the company directly by phone.
If your computer has been infected by malware, viruses or Trojans, or you’d like to improve your device’s security before an attack happens, contact Geek Rescue by calling 918-369-4335.
November 14th, 2013

Virtualization is becoming a staple of businesses of every size. According to a Cisco survey, 77-percent of small to medium businesses have already virtualized part of their infrastructure. In the next two years, the virtualization budgets will increase for about 70-percent of all businesses. As Sam Narisi, of IT Manager Daily writes, virtualization allows companies to save money while increasing flexibility and scalability, but there are some security concerns. Here are the top three security issues associated with virtualized services and how to overcome them.
Many organizations host multiple virtual machines on a single physical machine. This is the nature of virtualization and why it is so popular. This opens the door for devastating attacks, however, if the virtual machines aren’t properly separated. It’s important to grant employees access to only the VMs they need. This way, if their access is compromised, your entire virtualized infrastructure isn’t.
Any software will contain bugs and vulnerabilities that can be exploited by intelligent hackers. Virtualization software is no different, but allowing a hacker to use these vulnerabilities could prove much more costly than other software exploits. Patches and updates are constantly being made available to fix these flaws. It’s important to stay current and update your software each time a new patch is released so you can close holes in security before an attack takes advantage of them.
More than ever before, it’s important to have a firm grasp on the IT assets in existence and who has access to each in your company. This was a simpler job when each machine was physical. With virtualization, VMs can be created and moved quickly, which sometimes leaves IT out of the loop. If a problem comes up, it’s much easier to solve it when you know where each machine is and who is able to access it.
Virtualization offers a number of benefits for businesses, but it also comes with increased responsibility and security concerns. Geek Rescue helps take the uncertainty and labor out of virtualization. Call us at 918-369-4335 to find out what services will give your business a competitive advantage.
November 13th, 2013

Apple’s OS X Mavericks features ‘Finder’, which is your primary tool for navigating the operating system. It’s not particularly jaw-dropping, or even exciting, but, as Thorin Klosowski of LifeHacker writes, it does offer a number of ways for you to be more productive and make OS X easier to use. Here are some of the most useful tips and tricks to get the most out of Finder.
A new feature in OS X is the use of tags. Any item you save, or is already saved, can have a tag added to it to help you stay organized. To manage all your tags, however, you’ll need Finder. Click on the ‘Finder’ tab at the top of the screen, then select ‘Preferences’ and ‘Tags’ from the menu. You’ll be able to delete tags, edit them, create favorites and organize them to your liking.
Finder is useful for so many jobs, you may need multiple tabs open at once. To do this, press Command+T and a new Finder tab will open. To navigate between tabs quickly, press Control+Shift and either the left or right arrow key.
By default, Finder shows your files in columns listed in alphabetical order by name, with date modified, size and kind also appearing. To add options and change the way files are sorted, go to the Finder menu, select ‘View’ and ‘Show View Options’ while you’re in a folder. Or, to change the arrangement altogether, go to ‘View’ then ‘Arrange by’.
The Finder Toolbar is highly customizable and it probably initially includes items you don’t need. To remove unused items, go to the Finder menu, select ‘View’ and ‘Customize Toolbar’. You can rearrange or remove items completely. To add items, including files, folders and apps, select the item, then Command+Click drag it to the toolbar.
These tips help you customize your Mac to make it easier to use. If you encounter problems like broken hardware, decreased performance or malware, bring your machine to Geek Rescue or call us at 918-369-4335.
November 13th, 2013

Microsoft’s latest operating system, Windows 8, has some great features, but there’s room for improvement. As Preston Gralla of Computer World writes, Windows offers some built-in tools for boosting performance if you know where to look. The first step is to unhide them.
To do so, press the Windows key and ‘I’ to bring up the settings. Click on “Tiles” and change “Show Administrator Tools” to ‘Yes’. This gives you access to some of Windows more complex, powerful performance tools, but also opens the door to disrupting your system. If you’re a novice user, it’s probably best to leave this to a professional. Even if you are more advanced, it’s a good idea to go back and hide Administrator Tools after finishing the work outlined here.
This tool has been available since Windows Vista and lets users see what applications are using the most resources. By typing “resmon” at the Start screen, the Resource Monitor icon will appear. Once opened, you’ll see a list of all of the apps and services currently running and a graph of your computer’s used resources. With this information, you can make informed decisions about which applications can be closed to improve performance. You may also decide that a replacement is needed for a particularly taxing program.
Also available since Vista, the Reliability Monitor is for tracking system stability and monitoring crashes. Access it by typing “reliability” at the Start screen, then click ‘Settings’, then ‘View Reliability History’. You’ll see a graph of your system’s stability with a rating between 1 and 10. Each time there’s a application or system failure, the rating drops. Every day there’s no crashes, the rating improves. In addition to this simple rating system, you’ll be given a list of all of the failures your system has experienced. You’ll be able to read details of each. By studying this report, you’ll be able to see where fixes and changes are needed.
For many users, their system starts slowly because they’re asking too many programs to load automatically on start-up. To thin this list, use the Task Manager. There are many ways to access it in Windows 8, but perhaps the easiest is the classic ‘control-alt-delete’. Click the start-up tab once in Task Manager, which you may need to click “More details” to see. This tab shows you what programs are asked to launch upon start-up. You’ll also see an impact rating, which judges how much each application slows start-up time and how much disk space it takes to load. Use this information to only load programs you constantly use and don’t greatly impact start time.
Even though it should be enabled by default, it’s also a good idea to check that you’re using Fast Startup. Rather than closing all sessions when you shut down your computer, Fast Startup saves your Windows kernel session to disk, which is called hibernating. This session is loaded when you start-up again to cut the time it takes to restart. To check if you’re using Fast Startup, type “Power” at the Start screen, then click ‘Settings’ and ‘Power Options’. From there, click ‘Choose what power buttons do’ and the Fast Startup option will be under ‘Shutdown Settings’.
The Task Manager itself is also a powerful tool in Windows 8. It contains tabs to track each user, the performance of your CPU, Memory, Wi-Fi and more and to track the history and usage of applications. Again, using these tools incorrectly can have a negative impact on your system so be careful what you click.
For help getting the most out of your computer, or to fix a device that isn’t working correctly, call Geek Rescue at 918-369-4335.
November 12th, 2013

You may have heard the latest smartphone rumors of a curved screen. Samsung will have the first curved glass offering, the Galaxy Round announced a month ago. Jason D. O’Grady, of ZDNet, reports that the curved screen isn’t just a gimmick. It also offers an enhanced user experience.
First, the curve isn’t dramatic. The Galaxy Round features a screen only .10 inches away from flat, which is about equal to the curve of most handheld mirrors. This slight curve greatly reduces the negative effects of ambient light on the screen, however. This makes it easier to read, makes colors more true, improves contrast and more. The curved screen is also much easier to use outside in sunlight.
A screen that’s naturally easier to read has some additional benefits, as well. Most notably, battery life could be much better because screen brightness can be turned down without losing readability.
The iPhone 5S, Apple’s latest smartphone release, has been knocked repeatedly for poor battery life. There are already many rumors suggesting that a future iPhone will go the curved screen route.
Part of that speculation comes from Apple’s recent purchase of synthetic, manufactured sapphire and its construction of a plant in Arizona. Sapphire crystal is already used on the Touch-ID home button on the iPhone 5S. It’s regarded as tougher and more scratch resistant than Gorilla Glass, which is currently being used to make iPhone screens.
No matter what shape your smartphone’s screen is, Geek Rescue fixes it when it breaks. Call us at 918-369-4335 or come by one of our locations to get your devices working like new again.
November 12th, 2013

When you purchase a new computer, you’re probably expecting it to last for a few years before having to replace it. But how long can you realistically expect it to last? Brian Beach, of Backblaze, writes that they’re researching the average life expectancy of hard drives so you can have realistic expectations for your devices.
Before diving into the numbers of the study, it’s important to understand the hard drives being examined and how they’re being used. Backblaze tried using consumer-grade, internal hard drives, which would be the same as you would find in your PC. They ran into a shortage of these types of hard drives, however, so some are from external units. That could arguably alter some of the data found in their study, but considering there are more than 25-thousand drives involved, it likely won’t make that much difference.
Though the drives used are similar to what you’d find in your computer, they’re not used exactly the same way you use yours. Backblaze’s hard drives are kept spinning at all times. They’re used in data centers so there’s never any down time. So, their life expectancy is in time of use. If a hard drive is expected to “live” for four-years, that’s not four-years from purchase, but rather four-years of use, which in your PC could be closer to ten years from purchase.
There are three distinct phases of a hard drive’s life. In the first phase, which is the first 18-months of life, five-percent of hard drives are expected to fail. These are mostly drives with a factory default that cause them to break.
In the second phase, which extends to the three-year mark, hard drives actually fail less. During this second phase, the average fail rate is only about 1.4-percent. In this phase, the factory defects have all been weeded out. The failures that are seen are attributed to random failures, which are freak accidents that can’t be planned for or avoided.
The third phase begins at the three-year mark and contains the highest failure rates. Up until year five, failures hover between about 10-percent and 18-percent. This is where Backblaze’s data ends. They’ve only been monitoring hard drives for four years, but speculation says year five marks another increase in failure rate.
- How long will your drive last?
This research seems to suggest that any hard drive you purchase has a chance of breaking at any time, with the chances increasing significantly after three years. That’s true, but overall 80-percent of hard drives last for at least four years. An informed estimation is that at least half of hard drives will survive for six years.
Remember that this is referring to time of constant use. If you’re fortunate enough to buy a hard drive that will last more than six years of use, you’ll likely have no problems with it before you’re ready to buy another computer.
The threat of a hard drive failing is constant, however. One in five won’t make it to year four. Unfortunately, there’s no user practices that can extend the life of your hard drive. It’s just blind luck whether yours lasts or doesn’t, assuming you aren’t being unnecessarily hard on it. That underscores the importance of backing-up your files. Given that your hard drive could fail at any time, using your hard drive as a storage option isn’t as reliable as you might think. Instead, be sure to explore other storage options before your hard drive crashes so you’re not left with nothing.
Geek Rescue offers a number of storage options and we also fix hard drives. We’ll recover lost data and get you back up and running in no time. Bring your broken devices in to on of your locations or call us at 918-369-4335 today.
November 11th, 2013

A zero-day exploit that affects Internet Explorer, Windows XP and Windows 7 users won’t be getting a patch from Microsoft any time soon. Microsoft’s Patch Tuesday for November is only a day away and, as Paul Ducklin of Naked Security reports, news is already spreading that a patch for this exploit won’t be included.
The “remote code execution vulnerability” is dubbed a zero-day because hackers were the first to discover it. Rather than security experts, or Microsoft themselves, discovering the vulnerability and patching it, cyber criminals have been able to launch attacks in the wild before any precautions could be taken.
The attacks seen so far that exploit the vulnerability use .TIFF image files that contain malware. When a user opens the seemingly innocent image file, malware infects the machine, but no warning or notice is given. This silent infection allows hackers to remain undetected while they claim access to files and control a computer remotely.
So far, most of the attacks stem from email attachments. The .TIFF is hidden in a Word document and automatically loaded when the document is opened. There are a number of other ways the exploit could be attacked, however. Inserting the infected image file directly into the body of an email could infect your system through only a preview of the message. Hackers could also set-up websites specifically to infect visitors, or insert malware into existing sites using .TIFF images.
While there’s no patch coming from Microsoft this week, there are ways to protect yourself. A Fix it tool released by Microsoft will tell your computer to stop processing .TIFF files. This is a broad stroke, but one that will ensure the vulnerability will be closed until a more permanent patch is made available.
In the meantime, some simple advice will also help improve your security. You should always be wary of unsolicited emails and their attachments. Often, all it takes is opening the email to try to verify its authenticity is all it takes to become a victim. Also, make sure you have an antivirus program in place and it’s updated. Because of the way this exploit gives a hacker access to all of the files you’re current user account is able to access, it’s useful to use a non-administrator account. That way, if you are attacked, only part of your system is at risk, and solving the problem from an administrator account is much easier.
If any of your devices are infected with malware, bring them to Geek Rescue or call us at 918-369-4335. We’ll find the problem, fix it and help you protect yourself from future attacks.
November 11th, 2013

Software companies like Microsoft, Apple and Adobe release patches regularly to fix bugs and close security vulnerabilities. This is a common practice, but as Tyler Reguly of TripWire’s State of Security blog reports, Microsoft often makes a mess of it.
There are a number of factors that contribute to the confusing nature of Microsoft’s patch practices. Patch Tuesday occurs once a month and involves the patching of multiple Microsoft products and fix multiple vulnerabilities at a time. The downside to this bulk patch release is that new vulnerabilities that crop up are left open for weeks while users wait for the next Patch Tuesday to come around. There have been instances in the past when Microsoft has pushed out a patch outside of this schedule and other companies follow a similar patching process, but users are still left in the lurch from time to time.
In addition, patches are far from uniform. Microsoft could release multiple patches to fix a single vulnerability in a single product, or they could release one patch per product for each instance of a vulnerability. Some patches replace older patches, but sometimes multiple patches are needed to replace a single patch.
In an attempt to simplify this process, Microsoft introduced a single service that would automatically update Windows users with any applicable patches for all Microsoft products in use on their device. This actually caused more confusion, however. A user who has enabled automatic updates might think they’re fully patched at all times, but that’s rarely the case. That’s usually because an older version of an application is being used that Microsoft no longer supports or that won’t work with automatic updates.
Unfortunately, users aren’t warned that applications aren’t being updated. Instead, it appears they’re patched and safe from vulnerabilities. In many ways, this makes them more susceptible to breaches than if they knowingly avoided all patches to begin with.
Keeping your devices and networks safe requires an investment. Geek Rescue offers help for improving security for your home or business. Call us at 918-369-4335.
November 8th, 2013

About a month ago, software company Adobe announced that hackers had gained access to passwords and log-in information for millions of accounts. Initially, the number of accounts affected was estimated to be around 38-million. As Jim Finkle reports at NBC News, that number is actually significantly higher.
Password security firm, LastPass, discovered the stolen customer data on a website for cyber criminals. In actuality, 152-million user accounts were compromised.
Adobe, which makes popular software like PhotoShop and Acrobat, downplayed the significance of the data breach. They claim many of the accounts who saw their log-in information stolen were inactive. Either the email or password was out of date, or the account was registered under false information in order to take advantage of one-time free use offers. The out of date log-ins total an estimated 43 million accounts. It’s unknown how many accounts were set up with fictitious information.
Still, Adobe has notified 38-million users that their accounts may have been compromised.
Regardless of whether the log-ins were up to date or not, security experts warn that the data stolen is still valuable to criminals. The data stolen can be used in phishing scams with relevant details included to make them more believable. There’s also the concern of Adobe passwords being used for other accounts. As one expert pointed out, a user may have registered with Adobe years ago and since let the account become dormant. However, they may use the same password for other online accounts, which a hacker could now have access to.
Some have suggested that Adobe didn’t do enough to safeguard customer’s data from an attack. While this is an example of what can happen when the proper security isn’t put in place at the business level, there’s also a wake-up call here for users. Regardless of how strong your password is, it’s still vulnerable. Hackers have a variety of ways of breaking into your accounts, and they don’t all involved brute force efforts to guess passwords. Also, failing to use unique passwords for each account leaves you much more vulnerable to hacking.
If you have a business that needs to improve your security to keep your data and your customer’s data safe from attack, or if you’d like to improve the security on your personal devices, call Geek Rescue at 918-369-4335.




















