September 24th, 2015
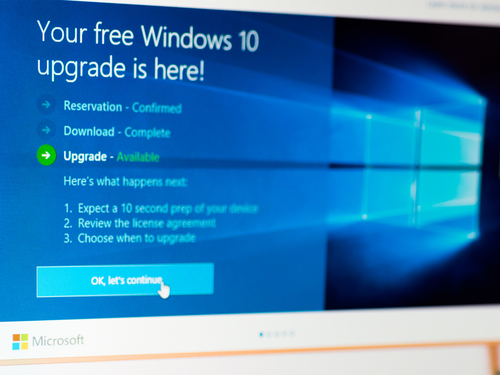
Microsoft began rolling out Windows 10 as an update to customers on July 29th. Not even two months later, the first example of a Windows 10 update being used as a smokescreen to distribute malware has been spotted. Specifically, this scam convinces users they’re downloading the Windows 10 update, when in reality they’re adding CTB Locker to their hard drives, which is a nasty form of ransomware. Here’s what you need to know.
The scam starts with an email, as many of these types of scams do. This one appears to be directly from Microsoft at first glance. While the email address appears to be legitimate and the subject reads ‘Windows 10 Free Update’, there are a couple of giveaways that this offer isn’t on the level. Most notably, if you’re already a Windows user, Microsoft probably isn’t going to contact you via email to distribute your upgrade. Think about how Microsoft typically offers updates to your current operating system. Rather than emailing you each time a new update or patch is available, these new files are either downloaded automatically or you’re notified directly on your desktop. If you’ve been paying attention, you’ve probably seen a notification giving you the option to upgrade to Windows 10 already.
If users fail to recognize this and follow the emails offer, however, they’re directed to a site to download files purporting to be Windows 10. It’s unclear how official this download page looks, but this is a good reminder not to download anything by following an emailed link. If this were a legitimate offer from Microsoft, you should be able to go to their official website yourself and find a way to download the update. Instead, users in this scam are downloading ransomware and then installing it on their devices.
With CT Locker unleashed, users see a warning pop up that informs them that their files have been encrypted and a ransom is demanded in order to unlock them. This ransom is 2-bitcoins, or about $600 and users are given 96 hours to comply. After that period, files are presumably lost forever. In most cases, these files aren’t unlocked and the malware isn’t made dormant even when a payment is submitted.
These emails have been spotted by users in the US, Russia, India, France and a number of other countries. While this is the first instance of Windows 10 being used in a malware scam, it’s not likely to be the last. The Windows 10 update is a perfect opportunity for cyber criminals to use these types of scams while users are already expecting to download files.
If any of your devices have been infected with malware and viruses, or just aren’t working the way they should, stop by and see us at Geek Rescue near 61st and Memorial, or give us a call at 918-369-4335.
September 18th, 2015

Apple’s latest version of iOS became available earlier this week. If you’re still wondering whether or not it’s worth it to download iOS 9 for your Apple device, browse through this list of features compiled by Gizmodo. Here you can see a non-exhaustive list of what you can do with iOS 9 that was impossible with iOS 8.
Now it’s easier than ever to use two apps at once. The Slide Over feature is designed for iPad users and brings up a second app as a sidebar. Just swipe your finger from the right edge of the screen in. For iPad Air 2 and iPad Pro users, Split View is available by tapping and dragging the app currently using Slide Over.
Android users have had the advantage of an always available Back button to return them to the previous screen or website. Now, Apple has introduced an easier way for their users to do the same thing. With iOS 9, a Back button is available in the top left corner of the screen at almost all times. Now, instead of double tapping the Home button, you can just hit Back to go between Apps.
- Write on email attachments
When you open an email attachment, you can now draw or write on it using the Markup feature. When you open an attachment, look for the Markup button. If it’s not there, try pressing and holding on the attachment. Using this tool allows you to draw with your finger to highlight, edit or make notes.
In past versions of iOS, you could pinch and zoom images, but not video. Now, pinch and zoom almost anything. That’s not the only video upgrade either. Open Settings>>Photos & Camera>>Camera for alternative ways to choose video and slow-motion recording modes.
Safari now supports mobile ad blockers, or Content Blockers as they’re referred to in Settings. These work similarly to ad-blockers that have been built into desktop browsers for years. This makes an even bigger impact on your phone where resources are constantly at a premium. The only catch is that Apple doesn’t supply a Content Blocker to users. You’ll have to go find and install one yourself.
If you’re running low on battery, but you’re no where near a charger, this iOS 9 feature will be a lifesaver. Low Power Mode can be activated and add up to an hour to your battery life. By turning off some background processes, you’ll get to use your phone for longer and generally won’t notice much of a difference in performance. You can tell when Low Power Mode is on because your battery icon in the top right corner will turn yellow and you’ll see a percentage of the battery that’s left.
To be fair, you could read the news just fine in iOS 8. However, iOS 9 is bundled with a brand new News app that offers some additional features to make reading the news easier. Content included is curated from carefully chosen partner publishers and articles are specifically formatted for your iOS device.
There are many additional features and capabilities you’ll get when you upgrade to iOS 9 too. If you experience any difficulties, bring your device to us at 61st and Memorial and we’d be happy to help. We’ll also keep your older devices running in case an upgrade isn’t in your near future.
September 10th, 2015

When you download an app for your smartphone, do you take the time to read the list of permissions? Most of us may quickly skim the permissions but ultimately fly by it like we do a new iTunes agreement. Doing so could leave your phone vulnerable to a variety of malware attacks and the latest threat to Android users is intelligent and could cost you hundreds of dollars.
It’s called Android.Trojan.MKero.A and it’s made its way into the official Google Play Store and infected legitimate, trusted apps. No one has been able to figure out how its infiltrated the Play Store, but it’s been found in at least 7 apps. The apps it has attached itself to are popular enough to have been downloaded up to 500-thousand times.
If you’re wondering if the Play Store has security in place to keep malware threats like this out, it does. This particular malware has eluded Google Bouncer, the app vetting system, however.
It’s purpose seems to be to silently subscribe victims to premium text messaging services. These can cost anywhere from 50-cents per message to more than a dollar. They require a few steps to ensure the user is aware of what they’re signing up for and notifications to alert the user they’ll begin getting charged. This malware threat is able to navigate all of that, however, to keep the user in the dark while the service begins.
First, the Trojan is able to use multiple steps to bypass CAPTCHAs, which are in place to prevent this type of fraud. Then, it claims administrative privileges, which a user agreed to when downloading the original app, to block notifications from the premium service. At this point, the costly messages can begin and, if the user isn’t quick to act, can add up quickly.
Google has been alerted to the presence of this malware in the Play Store, but no further announcement has been made. Back in March, Google implemented new procedures designed to keep malware out of the Play Store, but they’ve proven not to be enough in this specific instance.
When you download an app, be sure to carefully read the permissions and reconsider downloading if it requires giving the app administrative privileges. It’s also a good idea to install a trusted anti-virus app that can scan your device for malware already present.
If you’re worried your device is infected or just isn’t performing like it used to, bring it to us at Geek Rescue. We fix all kinds of devices with software and hardware issues. Stop by our shop at 61st and Memorial in Tulsa or call us at 918-369-4335.
September 2nd, 2015

There are a number of tools and tactics that are key to keeping your data safe online. Your choice of browser is your first line of defense. While all browsers claim to offer secure browsers, and many can be tweaked and upgraded to become more secure, there are a select few that are inherently considered secure browsers. With the security they bring, these browsers also offer little in the way of extra capabilities, tools or options so they aren’t for everyone. But, if you’re only consideration is security, consider these browsing options.
With a name like Epic Privacy Browser, or Epic, for short, it better deliver a secure browsing experience. And it does by stripping out every possible extra feature. If you’re used to using Google’s Chrome browser, Epic will feel familiar, but it will also feel like a more minimalistic experience. To achieve its epic privacy label, this browser eliminates all cookies and trackers every time it’s closed. Searches are filtered through the Epic servers, which eliminates the possibility that an IP address can be connected to a search. It even uses SSL connections whenever possible to keep users safe on open Wi-Fi connections. The one notable downside is that Epic doesn’t include malware and anti-phishing protection that can be found on many other browsers. But for strictly private browsing without a risk of allowing your history or data to fall into the wrong hands, it’s tough to top Epic.
In addition to a number of intriguing security and privacy settings, Comodo’s browser entry also allows you to easily pick up where you left off with Chrome or Firefox. With the Dragon browser, Chrome users can use many of the same plug-ins and import their bookmarks and saved passwords. Firefox users can do the same thing with Comodo’s Ice Dragon browser. This results in a secure browser that also brings a variety of options and features, which is a rarity. Some users have complained that the additional bells and whistles are excessive, however, and potentially open holes in the browser’s otherwise staunch security. As for the actual security features, Dragon has a tool to filter suspect URLs as they’re accessed and allows you to use their SecureDNS servers for the browser and other applications if you choose.
Arguable the most well-known browser out of this group, Tor is built on a modified Firefox browser and is available to Windows, Mac and Linux users. Much like the Epic browser, however, its focus is on privacy rather than security. There are no anti-malware tools and does not block plug-ins. But, through hidden relay servers, Tor is able to keep users almost entirely anonymous provided they stay on HTTPS connections. Tor also comes with a drop in performance from other browsers. Really, it’s only concern is privacy at all costs, and there are several associated costs. But, what it claims to do, it does quite well.
If your chief concern while surfing the internet is that someone will be able to track your movements, or steal information from you, these browsers do an excellent job of security. They don’t all keep you from downloading infected files, but by using these in conjunction with other tools and being intelligent about your online habits, you can stay safe from most threats.
At Geek Rescue, we offer a range of services that help you overcome problems with your various devices. From malware infections, to hardware issues, call us when your computer, tablet or smartphone is acting up and we’ll make it work again.














